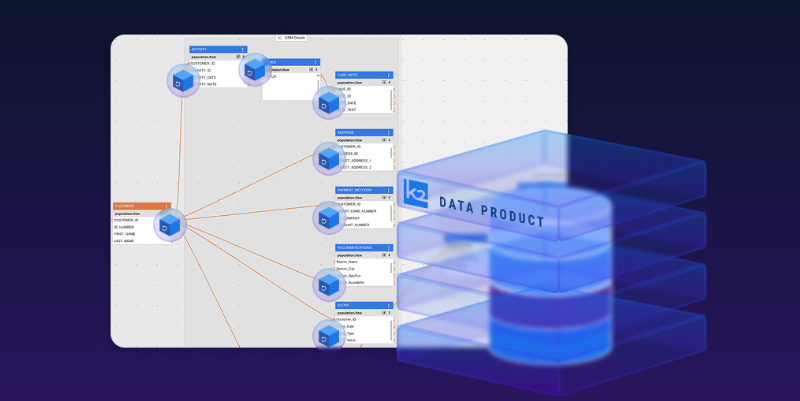
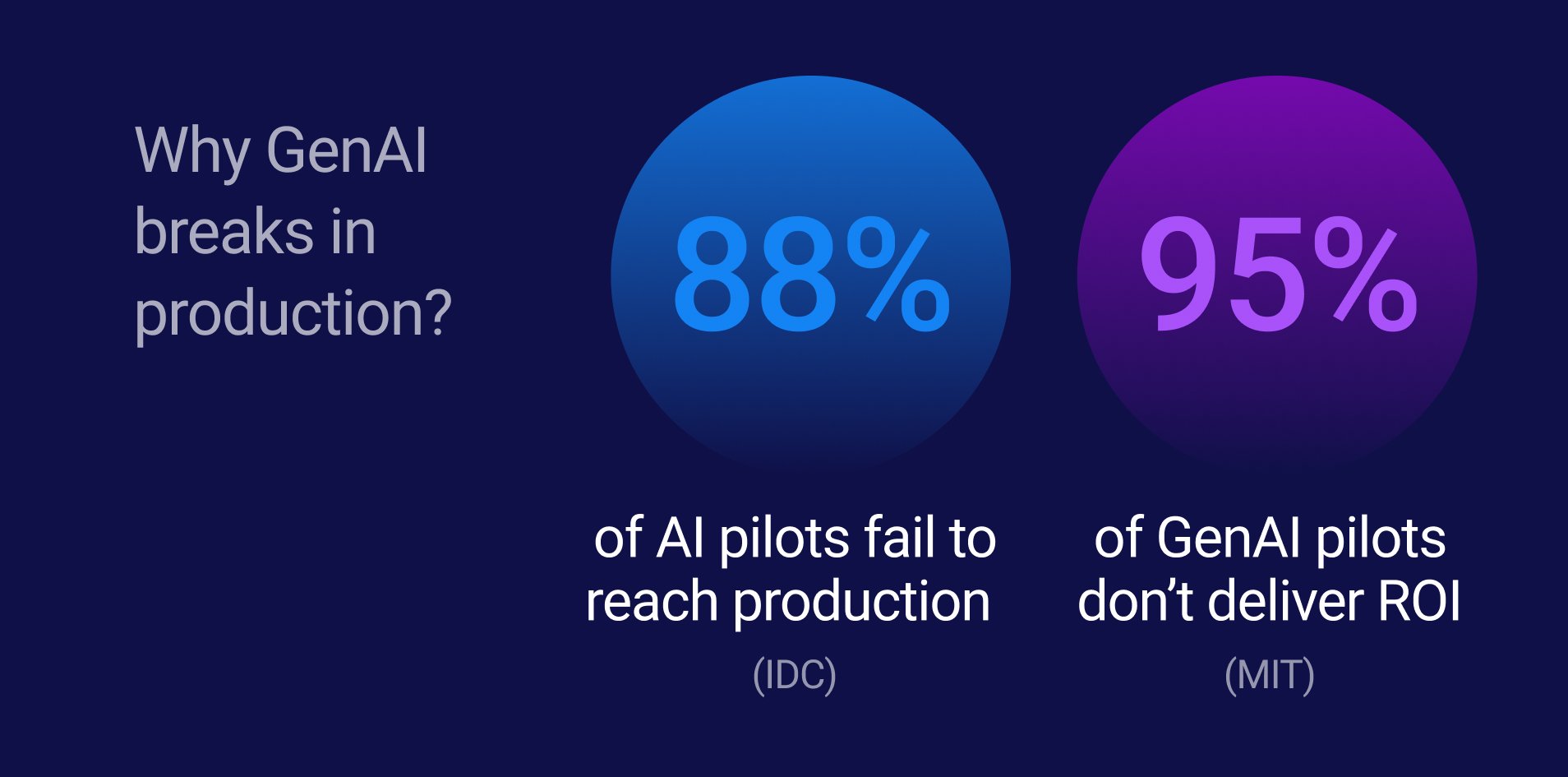
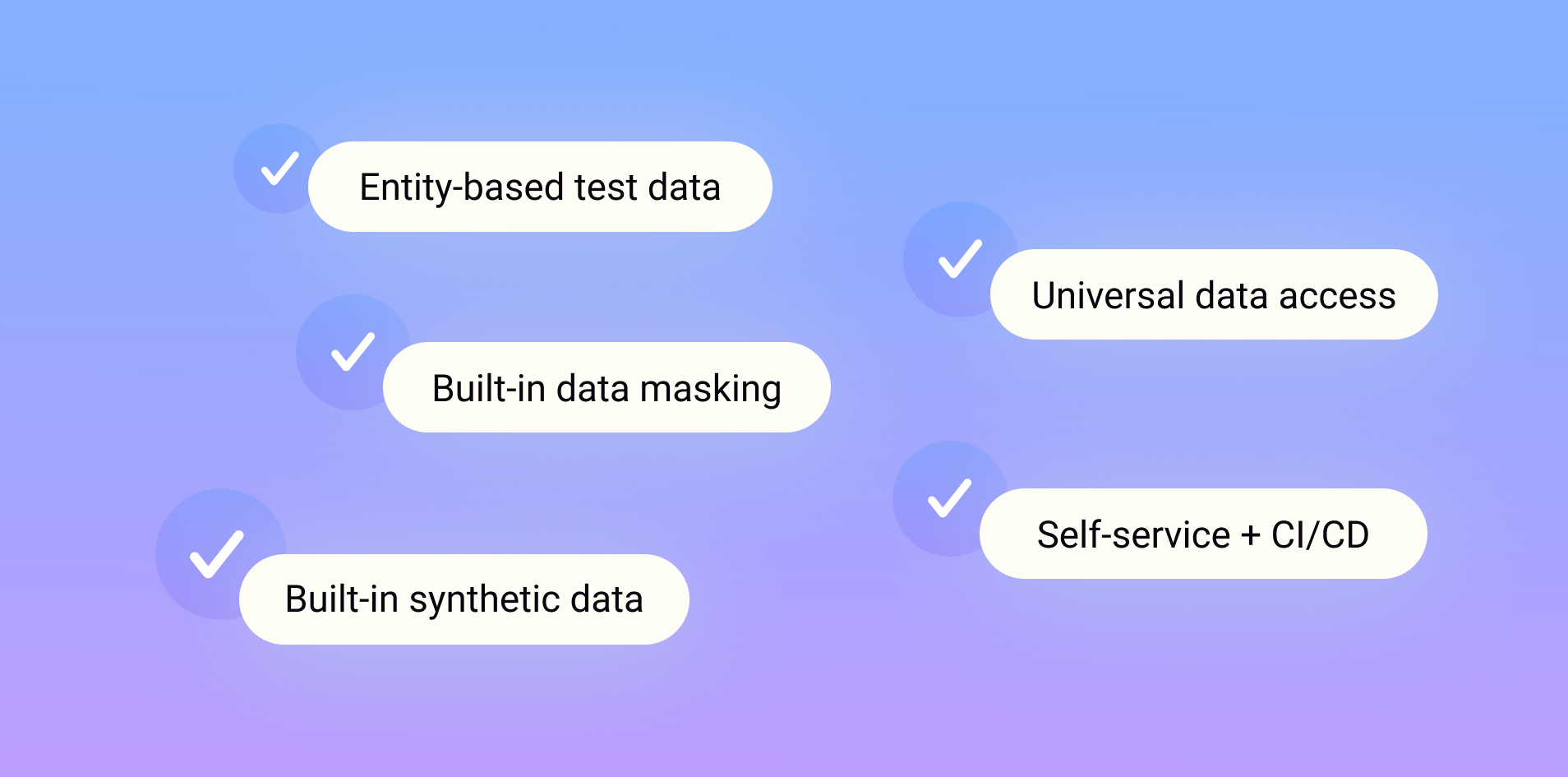
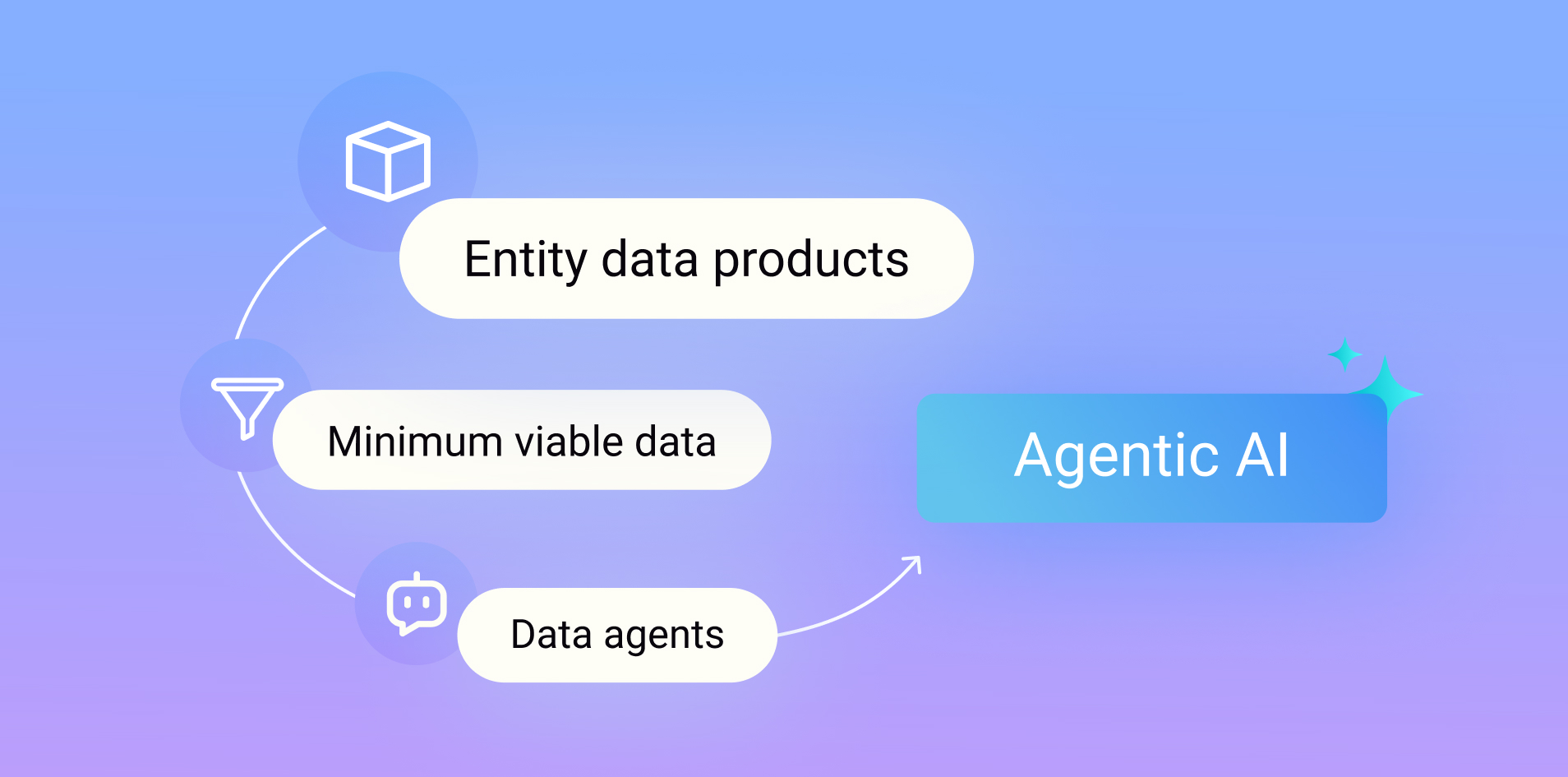
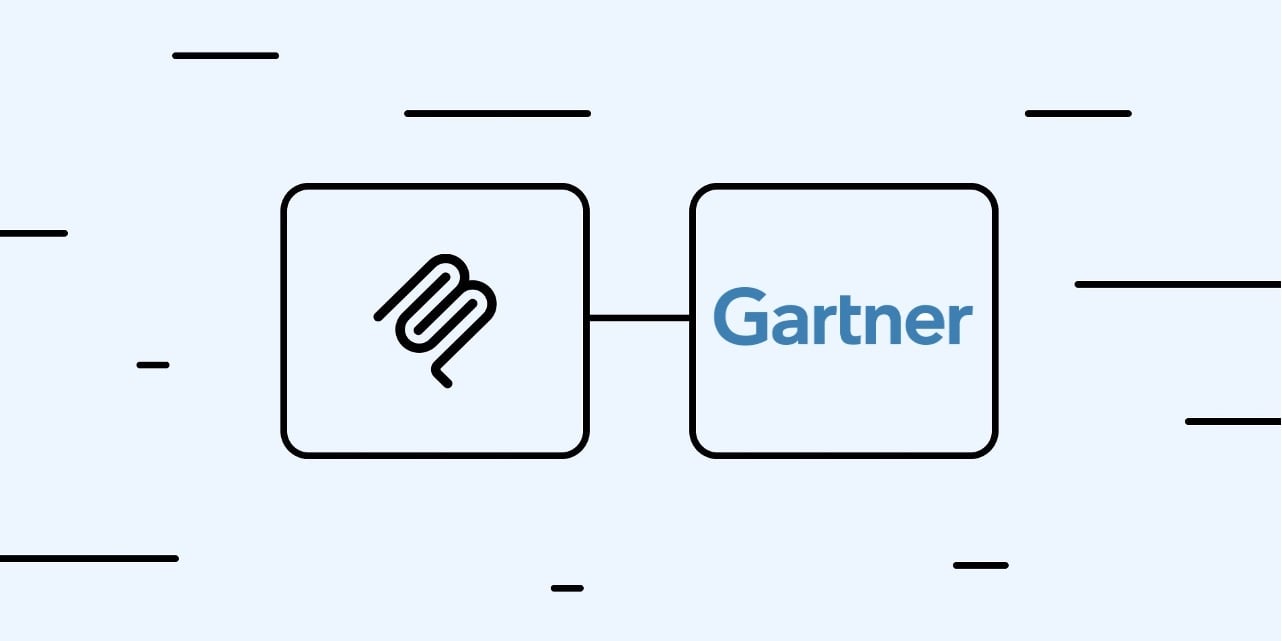
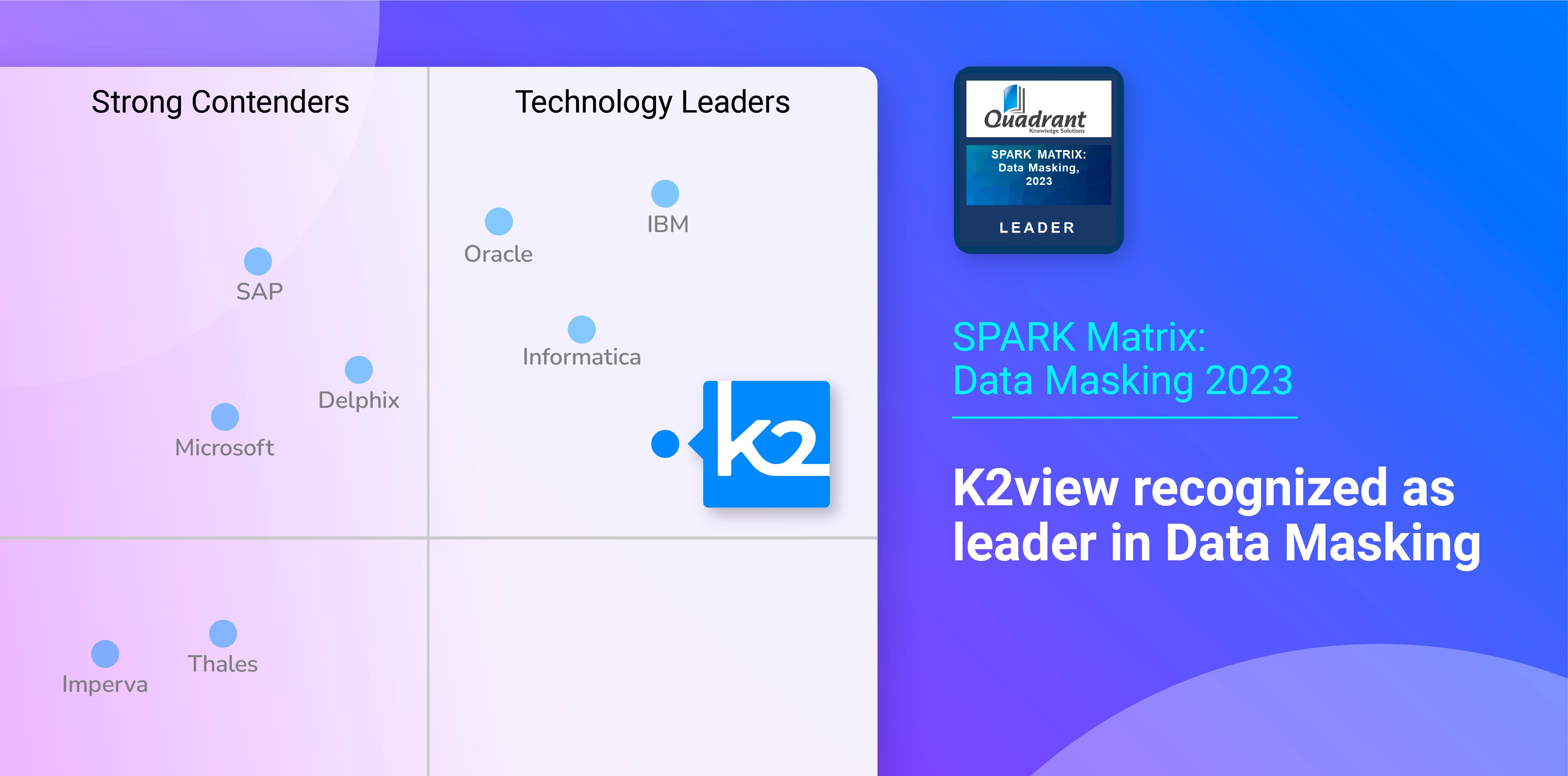
Gartner names K2view a Visionary in its Magic Quadrant for Data Integration Tools for the 3rd year in a row and rates us higher in our ability to execute.
- Platform
- Solutions
- Company
- Resources
Platform
Capabilities
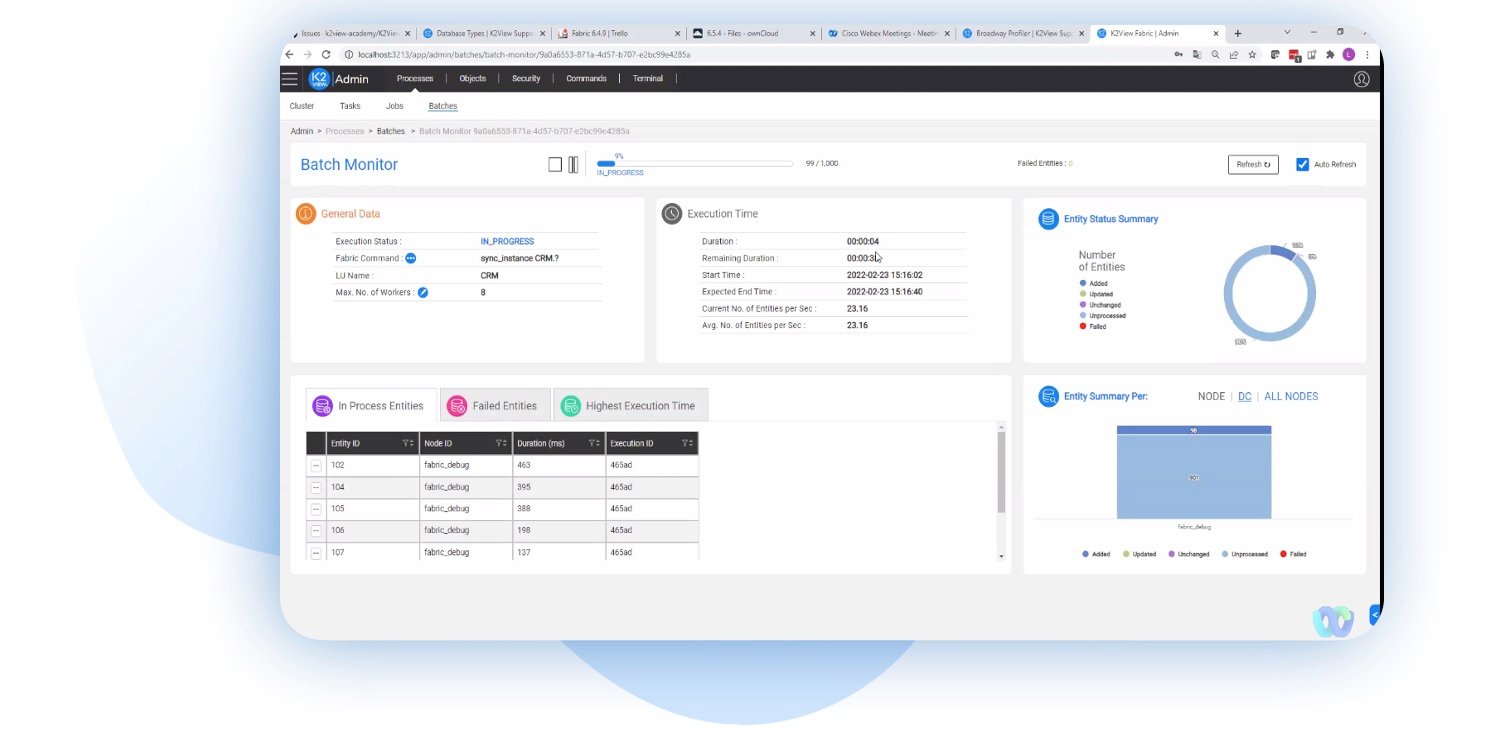
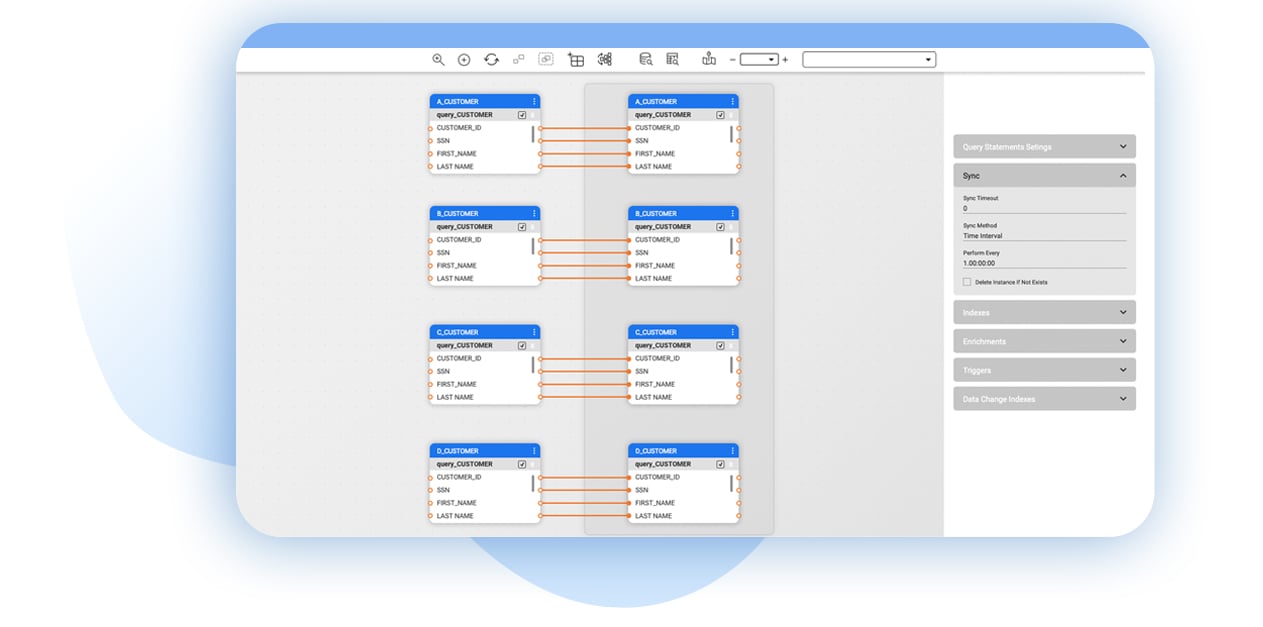
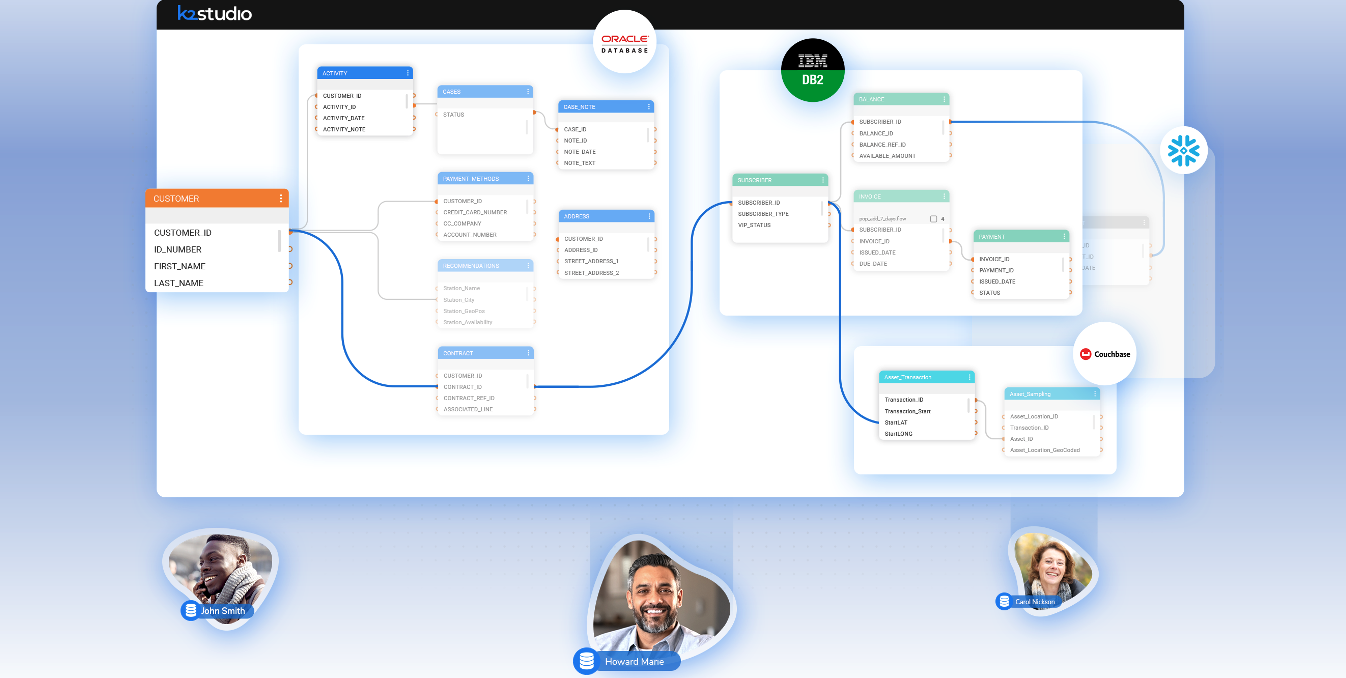
Architecture
Solutions
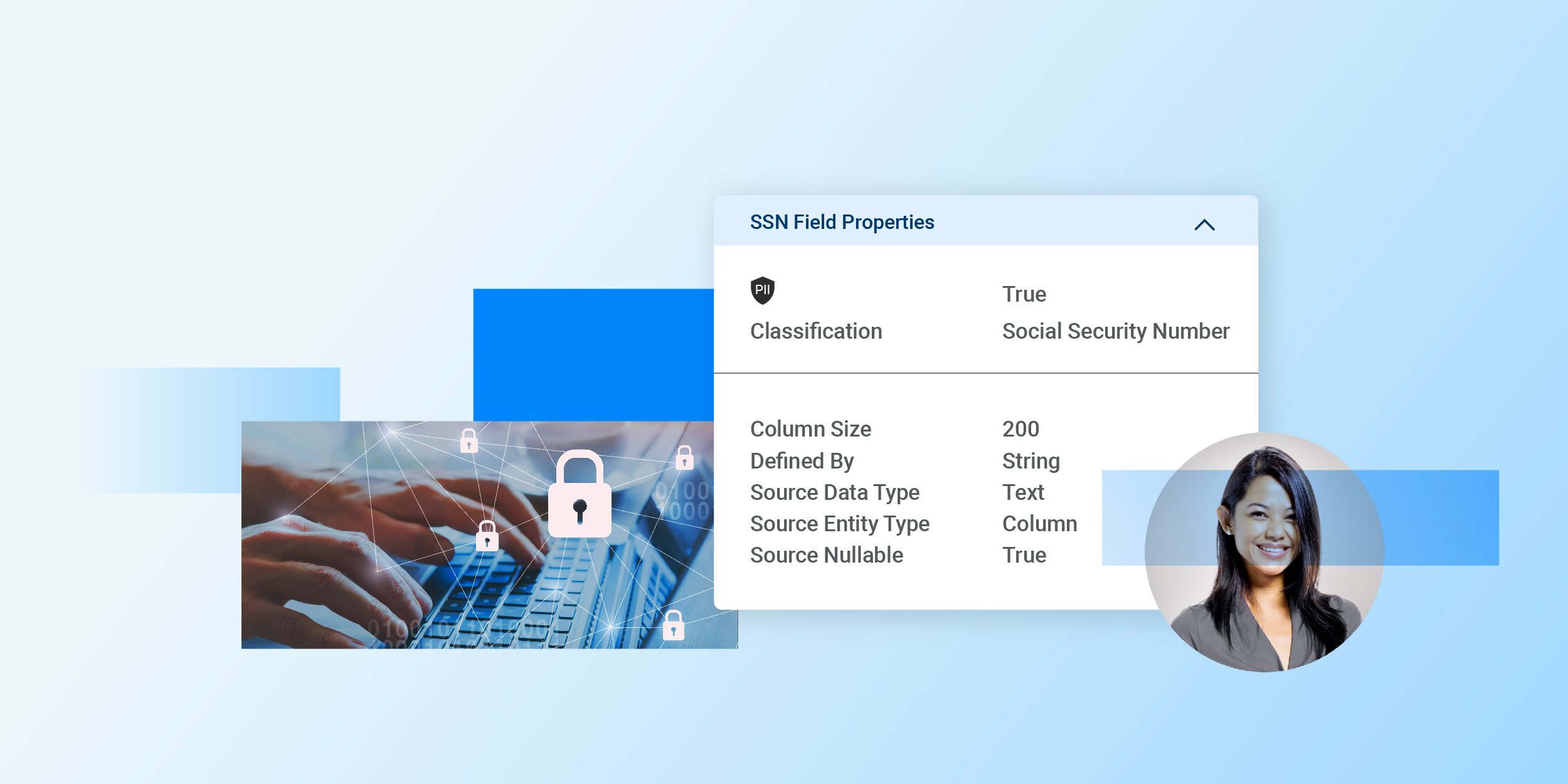
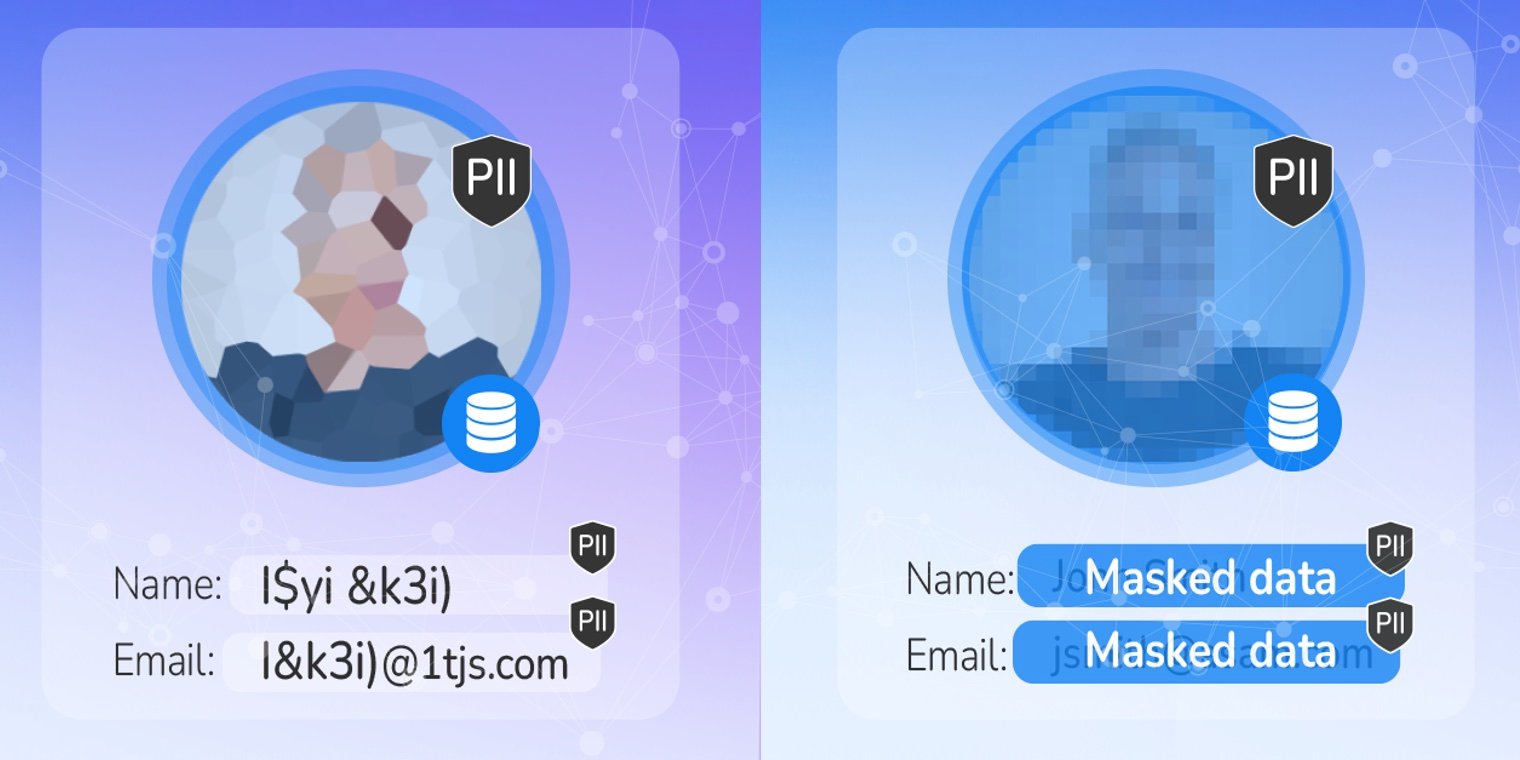
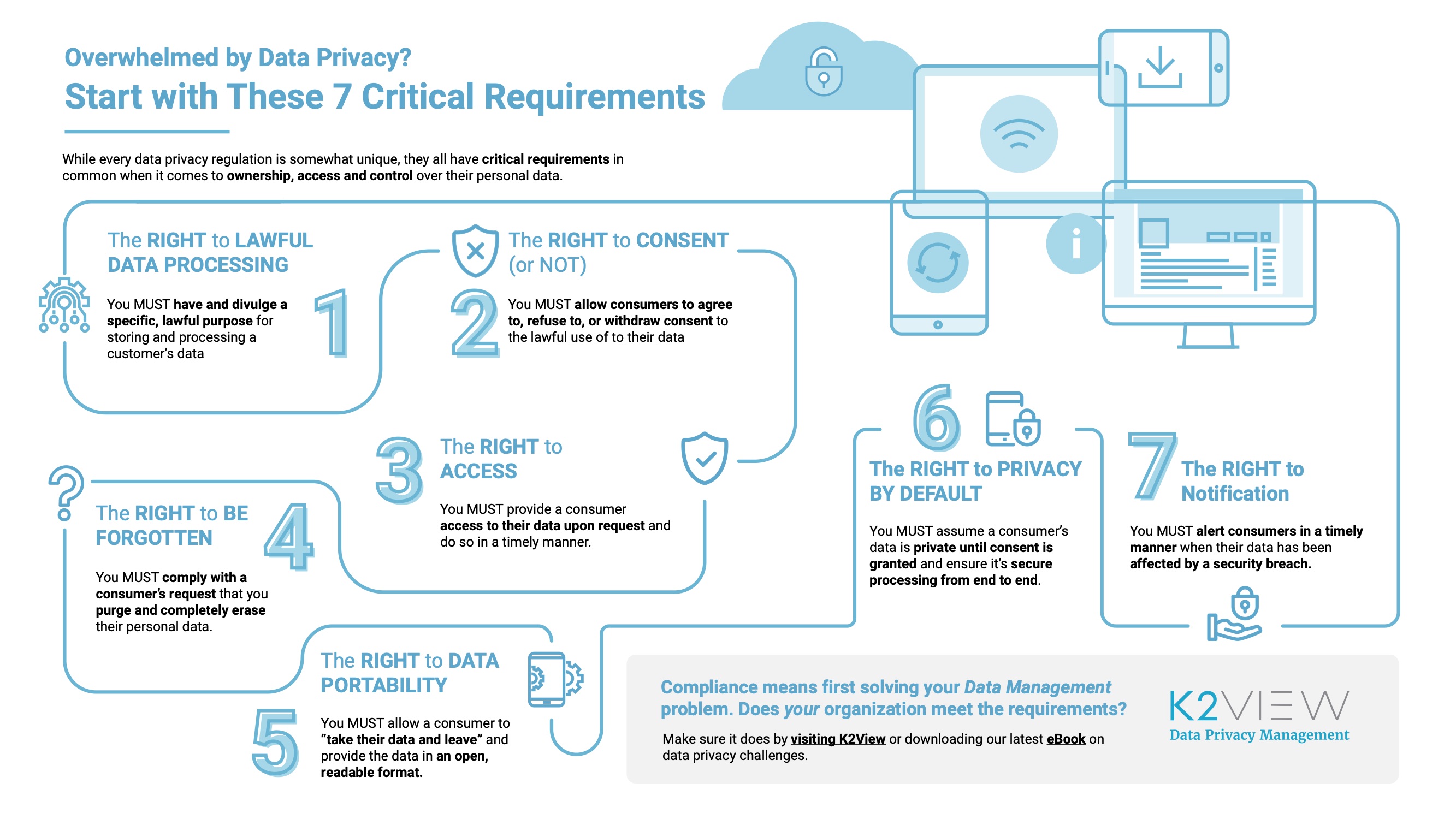
Data Privacy and Compliance
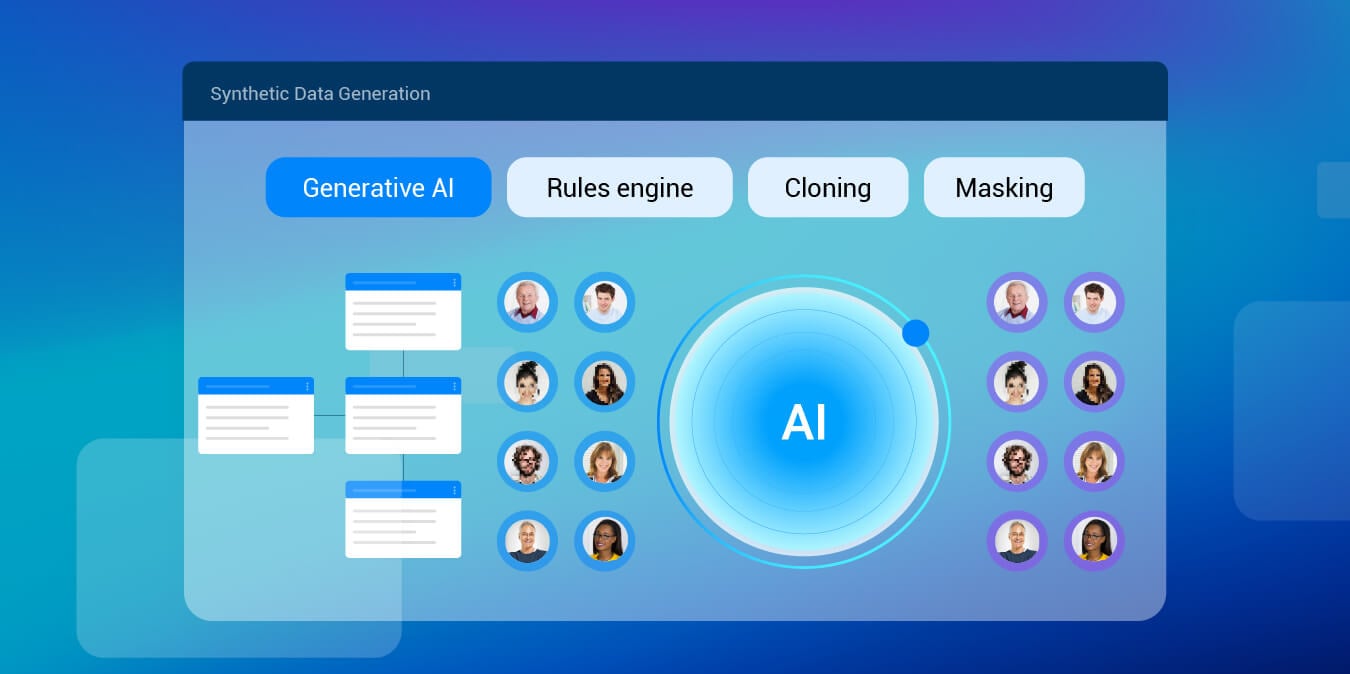
Data for Generative AI
Company
Company
Reach Out
Resources
Resources
Education & Training
- Platform
- Solutions
- Architecture
- eBooks & Guides
- Test Data Management (eBook)
- Data Masking (Guide)
- Data Anonymization (Guide)
- Synthetic Data Generation (eBook)
- Retrieval-Augmented Generation (Guide)
- Data Agents (Guide)
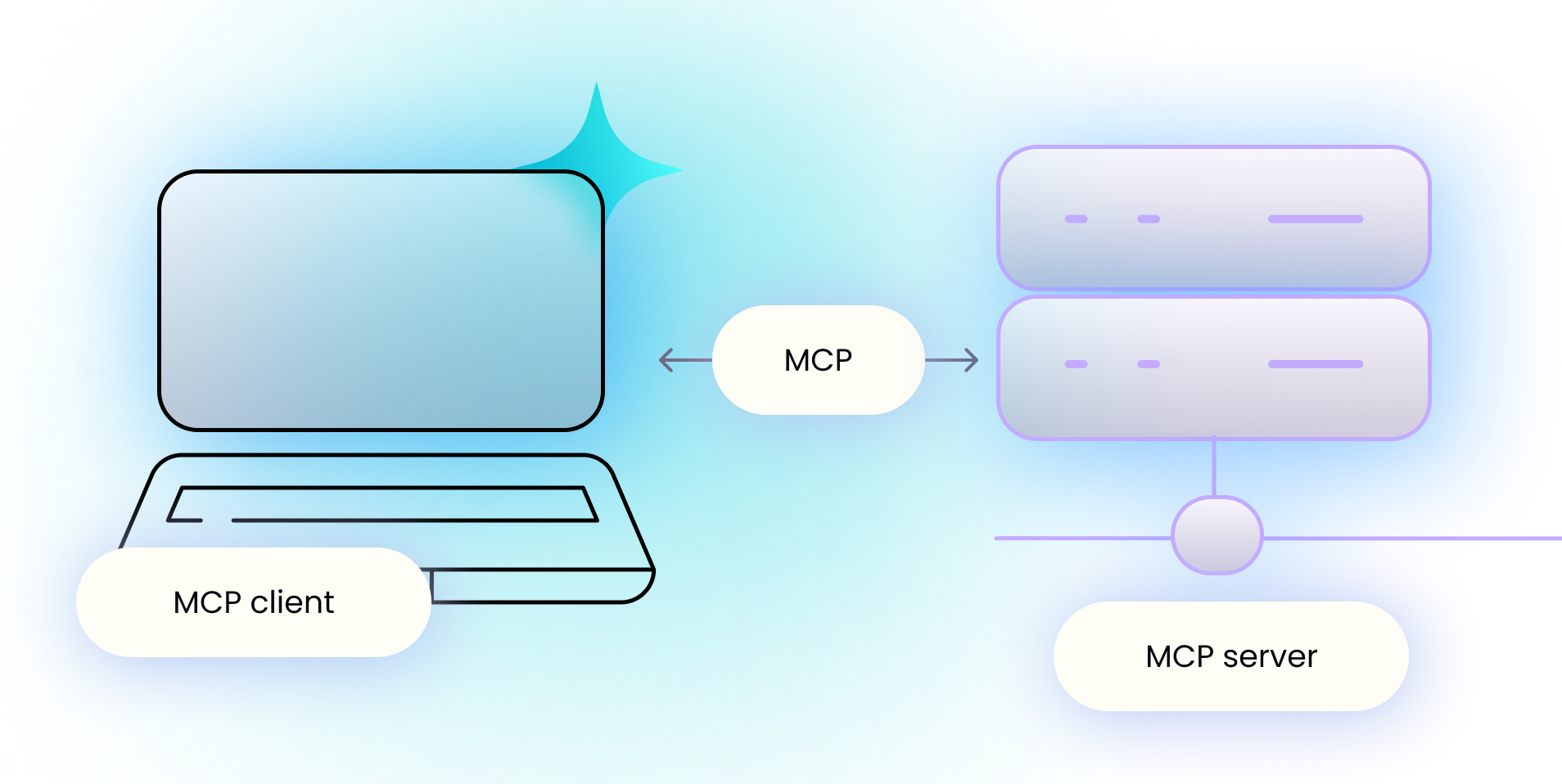
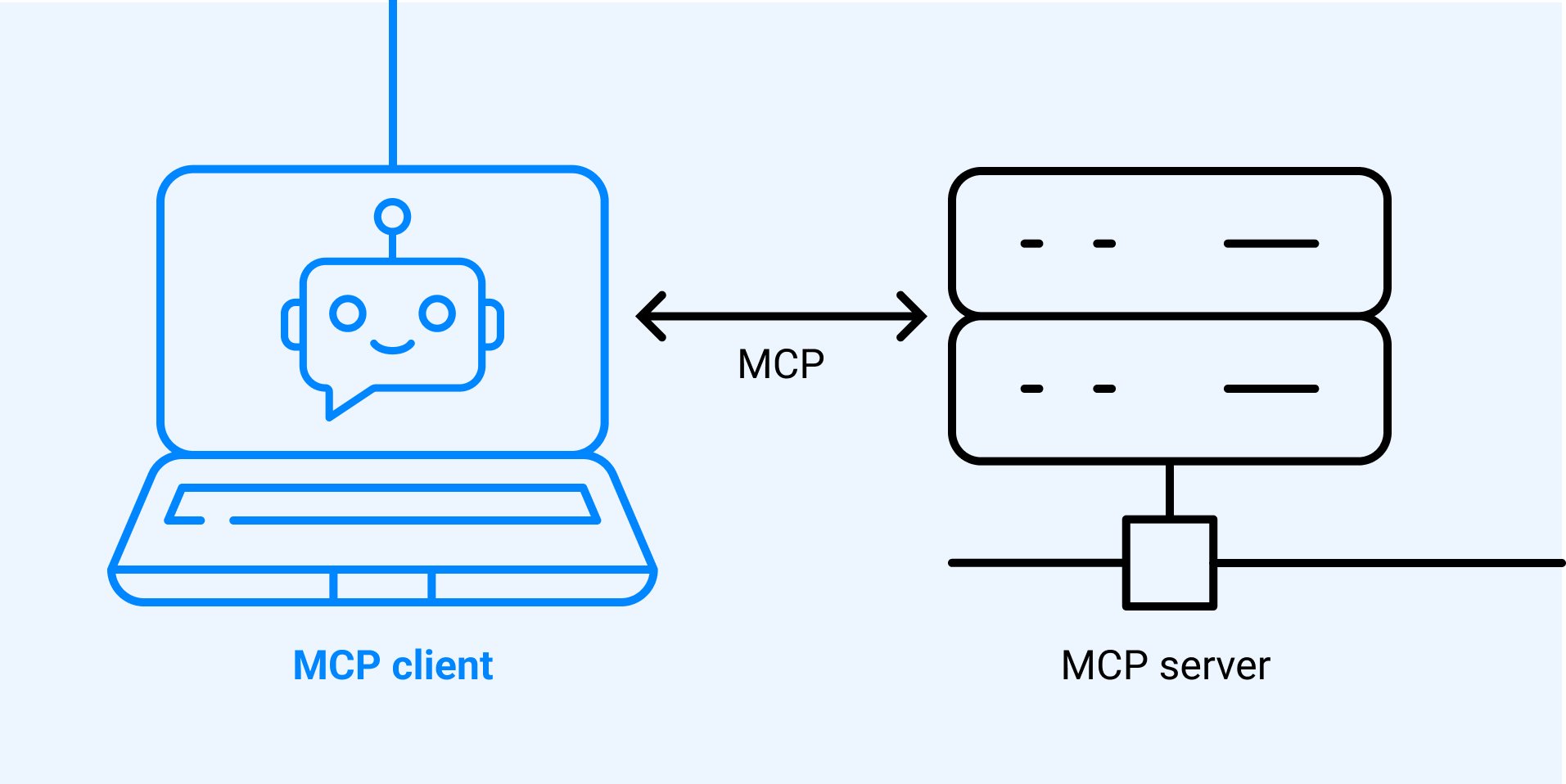
- MCP AI (Overview)
- Customer 360 (Guide)
- Data Products (Guide)
- Data Fabric (Overview)
- Data Mesh (Overview)
- Data Virtualization (Guide)
- Company