For global enterprises, complying with privacy laws is a daunting task. Learn how to simplify compliance, by aiming for the highest data masking standard.
Table of Contents
Only the Highest Data Masking Standard Will Do
Most Common Data Privacy Laws
Data Masking on an International Scale
Aiming for the Highest Data Masking Standard
Data Product Platform Sets the Data Masking Standard
Only the Highest Data Masking Standard Will Do
As regulations on data privacy and protection expand, businesses that handle consumer, patient, or employee data are being closely monitored. Today, enterprises are compelled to comply with a wide range of data protection laws, resulting in the need to anonymize data and restrict its access.
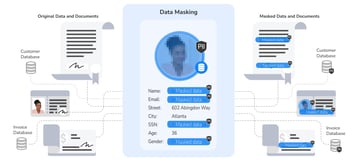
Data masking , also referred to as data anonymization, is one of the best ways to ensure compliance, and prevent security breaches. However, not all data masking solutions are equipped to comply with the full range of regulations your organization might be subject to. Because effective data governance is keeping companies to the highest data masking standard, choosing the right data masking solution – and data integration platform – is critically important.
Most Common Data Privacy Laws
Different countries and regions have their own regulations. But even if you do not operate in such geographies, your customers – and their data – might reside there. Or, your data could be transmitted through these regions via third-party vendors and external servers. That means you need to understand what these compliance laws are all about, as well as how to handle them.
Here’s a brief overview of some of the most common data protection and privacy laws that are in force today.
GDPR
The General Data Protection Regulation, enacted in 2018, is known as the toughest privacy and security law in the world. Although it was passed by the European Union, it applies to any organization in the world that targets or collects personal data from people in the EU.
GDPR defines personal data as “any information that relates to an individual who can be directly or indirectly identified,” such as names, email addresses, location information, ethnicity, gender, biometric data, religious beliefs, web cookies, and political beliefs. Failure to comply with GDPR can lead to heavy fines. For example, Amazon had to fork up €746 million; WhatsApp, €225 million; Google and affiliates, €200 million; and Facebook, €60 million.
CPRA
The California Privacy Rights Act of 2020 intends to secure privacy rights for California consumers, including the right to:
-
Know about the personal information a business collects about them and how it is used and shared
-
Delete personal information collected from them (with some exceptions)
-
Refuse the sale of their personal information
-
Exercise their CCPA rights, without bias or discrimination
CCPA applies to any commercial enterprise that does business in California, with a few conditions. For example, the company must have a gross annual revenue of at least $25 million, and derive 50% or more of their annual revenue from selling California residents’ personal information. Businesses are also required to give consumers certain notices explaining their privacy practices.
PCI DSS
The Payment Card Industry Data Security Standard is the global security standard for the credit card industry. Established by five major international payment entities in 2006 – JCB, American Express, Discover, MasterCard and Visa – PCI DSS is designed to protect customer data, as well as transaction data.
PCI DSS applies to any organization that accepts, transmits, or stores cardholder data, regardless of the size or number of transactions. Although compliance with PCI DSS is not federally mandated in the US, many states either refer to it directly, or rely on equivalent provisions.
HIPAA
The Health Insurance Portability and Accountability Act was enacted by the US Health and Human Services (HSS) Agency in 1996. It provides a national set of standards to prevent personal health information from being disclosed without a patient’s consent or knowledge.
HIPAA applies to a broad range of entities, including healthcare providers, health services, and healthcare clearinghouses, as well as the businesses associated with such entities.
Data Masking on an International Scale
If your organization operates in different geographic areas, collects or processes data from consumers in different regions, or transmits data through different geographies, your data masking solution needs to support global compliance.
Global compliance refers to a set of data governance practices that enables an entity to adhere to all the local laws and regulations that govern the country in which they operate. Data masking could factor significantly towards attaining global compliance.
So if data governance includes the rules, systems, and protocols for obfuscating data in accordance with data privacy laws, data masking provides the means to get it done.
Aiming for the Highest Data Masking Standard
Your data masking best practices should include all of the measures and capabilities necessary for fulfilling your data privacy obligations. At the same time, the data integration platform on which it resides should promote business continuity and agility, such as the ability to perform analytics and testing.
Here are 6 of the most important data masking requirements:
-
Performing ongoing risk assessments
A data risk assessment helps organizations understand the current state of its data security, and identify where improvements are necessary. By performing regular risk assessments, you’ll be able to clarify compliance shortcomings, and reduce risk. Some of the key steps in a data risk assessment are:– Creating a comprehensive inventory of sensitive data
(spoiler: with a platform capable of automatic discovery)– Classifying each instance of sensitive data
– Reviewing all relevant security and privacy controls, such as who has access
– Assessing whether data security policies are adequately enforced
– Identifying data retention violations
– Documenting privacy and security failures
-
Masking unstructured data
Vast amounts of enterprise data (up to 90%) is unstructured. A good deal of sensitive information can be found within unstructured datasets, such as in images, PDF files, drivers licenses, XML documents, chats, and more. If you can’t mask unstructured data, you’ll never be able to fully comply with all of the data privacy regulations you are subject to. -
Masking data dynamically
Dynamic data masking limits the exposure of sensitive data by masking it for all non-authorized users. Dynamic data masking significantly reduces the risk of a data breach, and noncompliance with data privacy laws, by automatically masking sensitive data for users without the right privileges. -
Allowing for different methods of data masking
Different data privacy laws have different standards and requirements for protecting sensitive information. And of course, there are the business needs, such as enabling call center representatives to validate customer identities when contacted. So you’d want to make sure that you can mask data in a variety of ways, such as via anonymization, pseudonymization, encrypted lookup substitution, redaction, etc. -
Enabling reporting and auditing according to regulatory standards
In addition to performing routine data risk assessments, it’s important to report on your data masking activities specifically. For example, you’d want to record all data masking instances, data dependencies, relationships, and applied data masking techniques. This information can come in very handy, especially if you experience a breach, or must undergo a compliance audit. -
Maintaining referential integrity
Relational integrity ensures that anonymized data retains the same characteristics throughout the organization. Such relational consistency simplifies compliance, protects the system from cyberattacks, and supports analytics.
Business Entities Set the Data Masking Standard
Enterprises that process, store, and transmit data across different geographies require a comprehensive data masking solution that automatically fulfills relevant local data protection requirements, such as GDPR, CCPA, HIPAA, PCI DSS, and more. With entity-based data masking technology, you can achieve global compliance while attaining the highest data masking standard.
Unlike other solutions, entity-based data masking doesn’t store sensitive information in a central vault or repository. Instead, it persists and manages an individual’s personal data in a unique, encrypted Micro-Database™ as part of its embedded functionality.
Entity-based data masking automatically discovers and maps all the relevant data attributes across all systems, including Personally Identifiable Information (PII). It dynamically enables both structured and unstructured data masking, while ensuring relational consistency.
For enterprises that aim to increase compliance and reduce risk, a business entity approach – with the ability to mask unstructured data in a variety of different data masking techniques – is a must.