Table of contents
Most organizations that take a modern approach to cybersecurity embrace the “assume you’ve been breached” mindset. This thought process is helpful as you think through how to best protect your organization and customer data.
Encryption obviously plays a critical role in protecting your data. That’s why K2View’s new encryption patent is a compelling innovation – it provides a new approach to data encryption that makes mass breaches significantly more difficult. But what does that really mean?
A Tale of Two Breaches
Traditional Data Management
Imagine a scenario where a hacker has gotten in your environment and is now looking to achieve a mass breach. A typical scenario looks a little bit like this – a hacker has gotten in, is essentially in front of a locked safe, and if they can crack the safe, they have the data. In this scenario, the hacker is now in possession of anything contained in that database – whether it’s names, addresses, credit card numbers, or personally identifiable information (PII).
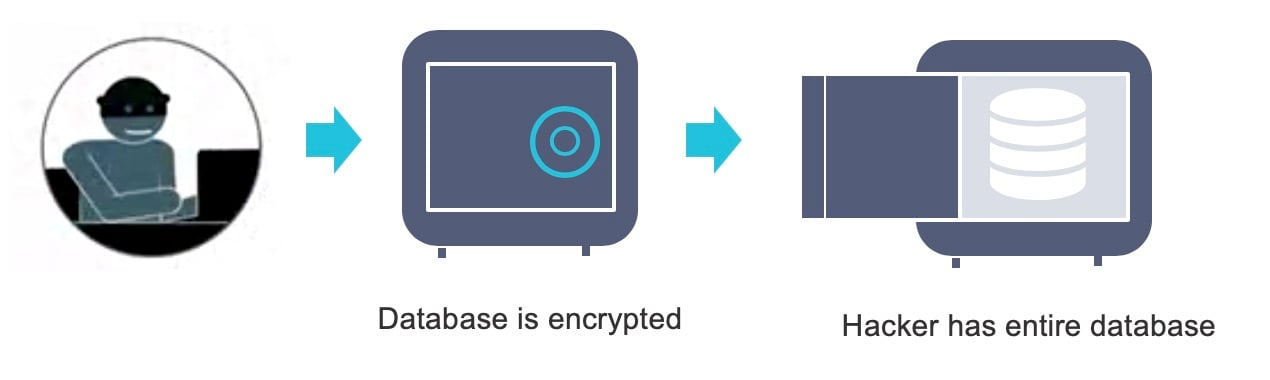
K2View’s New Patented Encryption Model
Now imagine the same scenario. Let’s say you have one million customers. A hacker has gotten into your systems and is now trying to hack your customer data that has been encrypted using K2View’s newly patented hierarchical encryption model.
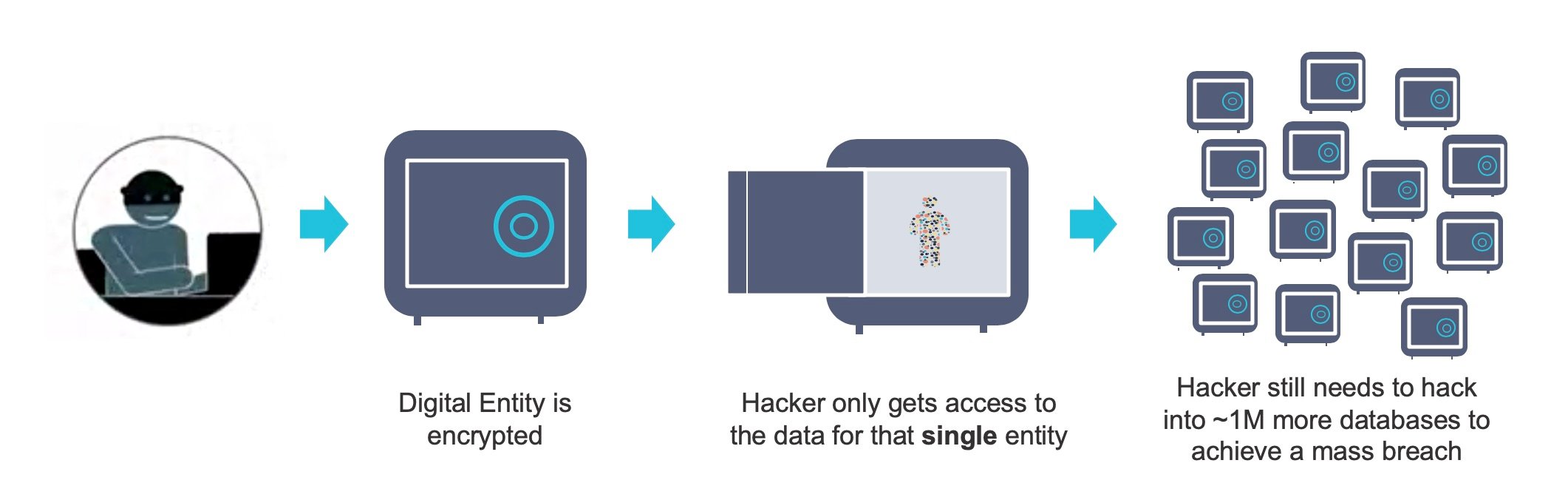
If the hacker is able to hack a Digital Entity, the person only walks away with the data of a single entity. For example, the hacker would only have John Smith’s data, instead of the data of every single customer in that database. This results in a significant effort to achieve a mass breach. An adversary would need to hack a separate datastore for every single customer you have. That means if you have 1 million customers, that’s 1 million datastores that would need to be hacked. Encryption is maintained while the data is at rest and while in RAM.
What fundamentally makes this approach possible is modeling data around a digital entity – a person, place or thing that has been recreated digitally out of its data. By rethinking how you manage the data, you can do things that were previously unheard of – like having a separate, encrypted database for every single customer, product, credit card, employee, or anything else that matters to your business. That’s what possible when you take a data-centric approach to how you manage data.
So, if you’re that security team that has to assume you’ve been breached, you may be able to breathe a little easier – at least when it comes to data contained in K2View.
Learn more about how K2View is changing data management in our overview paper.







.png)



