A practical guide to complying with the Digital Operational Resilience Act
What is DORA compliance?
Last updated on June 23, 2025
DORA compliance is the adherence to EU rules requiring financial institutions to manage ICT risks, report incidents, test resilience, and secure vendors.
01
Introduction to DORA compliance
The Digital Operational Resilience Act (DORA) is a regulation adopted by the European Union to strengthen the Information and Communication Technology (ICT) frameworks of financial institutions. While GDPR focuses on data privacy and protection, DORA is broader, concentrating on the resilience, security, availability, and integrity of ICT systems and the data they manage.
It applies across all EU member states and is enforceable within the European Economic Area (EEA) as indicated in the map below. DORA also affects non-EU companies that provide ICT services to EU-based financial entities, including global technology providers, cloud service vendors, and data processors that serve regulated firms within the European Union.

Source: EEA Europa
Here are some examples of EEA and non‑EEA firms that must comply with DORA regulations:
1. Global cloud providers
-
Google Cloud
UniCredit partnership across 13 markets
-
AWS European Sovereign Cloud
Launched in Germany to meet EU data protection and resiliency demands
-
Oracle Cloud
Offers IaaS, PaaS, SaaS to global banks
-
IBM Cloud
Says it’s financial‑services‑ready, serving BNP Paribas, Bank of America
2. Regional cloud providers
-
OVHcloud
French cloud specialist serving European financial institutions
-
Tresorit
Swiss end-to-end encrypted cloud storage used by EU firms
3. ICT providers
-
IXOPAY
Austrian payment orchestration platform partnering with EU banks
-
Salesforce
CRM platform used by EU financial services
-
SAP
ERP and data management supporting EU banks and insurers
-
Stripe
Global payment processor with strong EU footprint
These examples cover a wide range of ICT services – cloud, storage, payments, cybersecurity – which now fall under DORA jurisdiction if they support EU-regulated firms.
DORA’s global reach ensures any ICT provider, whether based in the Americas, Asia, Australia, or elsewhere, must align with EU operational resilience standards if serving financial clients there. These providers must establish EU legal entities, follow third‑party risk rules, as well as comply with testing and reporting obligations
DORA European regulations arrive at a time when financial services are increasingly dependent on digital infrastructures. From cloud computing to algorithmic trading, financial institutions operate in digital environments where any disruption has the potnetial to impact the entire economy. DORA ensures that resilience is not an afterthought but a fundamental part of operational strategy.
02
Why DORA compliance matters
DORA was developed in response to the rising complexity of digital ecosystems in financial services. Traditional capital buffers were not enough to counteract the effects of cyberattacks, system outages, or other ICT-related disruptions. Incidents such as ransomware attacks or system failures can compromise data integrity and erode customer trust. DORA fills this gap by creating a consistent and enforceable framework for digital resilience across the European financial sector.
DORA compliance aims to ensure financial entities can maintain operations during disruptive events, thus protecting the broader financial economy. This harmonization also simplifies compliance for cross-border operations, reducing the regulatory burden and maintaining a more unified cybersecurity posture across the EU.
Year over year breaches underscore the importance of DORA compliance, including:
-
Kingfisher Insurance
In October 2022, UK-based Kingfisher Insurance confirmed that a ransomware group stole 1.4TB of company data, including personal details of employees and customers. To gain access to the data, the cyberthieves accessed several email addresses belonging to staff, as well as passwords to Workday and Access.1
-
MOVEit
In May 2023, MOVEit, a managed file transfer software company, was attacked by a ransomware group which gained access to the sensitive data of over 2,700 organizations and 93.3 million people. The breach had far-reaching effects in the financial sector, emphasizing the risks facing the digital supply chain.2
-
Intesa Sanpaolo
Between April 2024 and February 2022, an employee at Intesa Sanpaolo – one of Italy’s largest banks – is alleged to have systematically accessed the account data of approximately 3,500 customers including many high-profile figures such as Prime Minister Giorgia Meloni, and her predecessor Mario Draghi.3
-
Adyen
In April 2025, Adyen, a Dutch payment processor, said its services were disrupted for about 8 hours over 2 days by a distributed denial of service attack which overwhelmed their European datacenters with traffic – peaking at millions of requests per minute – to render it unusable for visitors.4
These attacks illustrate the need for financial institutions to implement consistent, enforceable digital resilience standards such as the EU’s digital operational resilience act.
03
Key requirements for DORA compliance

Here are the 5 key requirements for DORA compliance:
1. ICT risk management
At the heart of DORA lies the need for a comprehensive ICT risk management framework. Financial institutions are expected to integrate ICT risk into their broader risk management strategies – meaning that they must identify all digital assets, assess potential threats, and implement control measures tailored to their risk profile.
Effective ICT risk management involves continuous monitoring and the use of automated tools to detect anomalies. Governance is key – senior management must not only approve these frameworks but also remain engaged in overseeing their implementation. This pillar ensures that digital resilience is embedded at both operational and strategic levels.
2. Incident reporting
The ability to quickly report and respond to incidents is crucial for containing damage and coordinating recovery. DORA requires financial firms to have formal procedures for detecting and classifying ICT-related incidents.
They must notify competent authorities promptly and follow up with detailed reports stating the timeline of the incident, its impact, the response steps taken, and lessons learned. This standardized procedure helps authorities assess systemic risks and coordinate responses at the national and EU levels.
3. Resilience testing
Testing isn’t just a one-off event. DORA mandates regular evaluations to ensure systems can withstand potential disruptions. Affected institutions must carry out basic vulnerability assessments and more advanced simulations, such as Threat-Led Penetration Testing (TLPT).
TLPT simulates sophisticated attacks to uncover hidden vulnerabilities in critical systems. These tests, conducted by independent parties, offer valuable insights into the organization’s preparedness and inform continuous improvements. Testing cycles vary according to company size and risk profile, ensuring a proportional approach.
4. 3rd-party risk management
Third-party ICT providers are a big part of financial operations, from cloud services to outsourced IT support. DORA recognizes the importance of these relationships and therefore requires participating companies to oversee them.
EU financial firms must perform due diligence before onboarding vendors and include clauses in contracts that address security requirements, audit rights, and termination protocols. Moreover, they must maintain a Register of Information (ROI) documenting all third-party arrangements. This register supports internal risk assessments and informs regulatory oversight.
5. Info and intel sharing
Cyber-attacks are rarely isolated. DORA encourages organizations to share information about emerging threats and vulnerabilities. While not mandatory, this collaborative approach enhances situational awareness and supports collective defense mechanisms across the financial sector.
Mandated organizations can participate in industry forums or EU-led initiatives such as the EU Systemic Cyber Incident Coordination Framework (EU-SCICF). These platforms foster a more responsive and resilient ecosystem by pooling knowledge and coordinating action
04
Step-by-step approach to achieving DORA compliance
To comply with DORA regulations, you must:
-
Understand your regulatory obligations.
-
Determine which of the 21 categories of financial entity you represent.
-
Identify your lead supervisory authority (EBA, EIOPA, or ESMA).
-
Build a compliance roadmap.
-
Conduct a comprehensive gap analysis to pinpoint shortcomings in your current ICT risk posture.
-
Develop policies aligned with DORA principles
-
Train your staff on DORA-related responsibilities
To maintain operational resilience, you ought to: -
Set risk tolerance thresholds.
-
Simulate incident scenarios.
-
Craft business continuity plans.
-
Assemble incident response teams.
-
Design escalation procedures.
To manage third-party risk, be sure to: -
Review all vendor contracts to ensure they align with DORA provisions.
-
Include clauses for data security, performance benchmarks, and exit strategies.
-
Conduct regular audits and risk reviews.
-
Monitor and adjust on an ongoing basis.
-
Track metrics such as downtime, response times, and vendor compliance.
-
Use dashboards to visualize resilience trends and adjust strategies accordingly.
05
DORA compliance enforcement and penalties
Non-compliance with DORA carries substantial risks:
-
Financial firms may incur country-specific administrative penalties.
-
ICT providers could face fines of up to 2% of their global turnover.
-
Supervisory authorities can suspend or terminate service agreements with non-compliant providers.
The following table shows the key penalty categories under DORA along with examples and details:5
|
Category |
Examples |
Details |
|
Financial |
Fines of up to €2 million for financial institutions |
Fines of up to 2% of annual turnover can be levied for severe lapses. |
|
Daily penalties of 1% of annual global turnover for non-EU ICT providers |
Enforcement is valid for up to 6 months, or until compliance is achieved. |
|
|
€250,000 for late incident reporting |
Timely notification is mandatory to prevent systemic risks. |
|
|
Administrative |
License suspension for non-compliance |
Regulatory authorities can suspend or revoke operational licenses for ongoing violations. |
|
Mandatory corrective actions |
Organizations may be forced to implement compliance measures at their own cost. |
|
|
Criminal |
Executive liability for gross negligence |
Directors or executives could be held personally liable for severe non-compliance. |
|
Potential imprisonment for systemic risks |
Gross negligence leading to financial instability could result in jail time in extreme cases. |
Here are the key enforcement takeaways:
-
DORA fines are substantial, often reaching millions of euros or a high percentage of annual global revenues.
-
Daily penalties accelerate urgency, underscoring that compliance is not a one-time event.
-
Both financial institutions and outsourced providers, including global cloud firms, can be penalized.
-
Timely reporting and robustness of ICT risk management frameworks are frequently the focus of these penalties.
06
DORA vs GDPR vs NIS2 vs EBA vs EIOPA
DORA is specifically designed to enhance digital operational resilience in the financial sector. It fills regulatory gaps by providing a unified framework for ICT risk, third-party management, incident response, and operational continuity. While several other regulations touch on aspects of ICT and cybersecurity, DORA consolidates and elevates these responsibilities across the EU financial landscape.
GDPR (General Data Protection Regulation) is a comprehensive privacy law that governs the processing and protection of personal data. It applies to all sectors and focuses on the rights of individuals and the obligations of organizations handling their data.
NIS2 (Network and Information Security Directive) aims to improve the cybersecurity of critical infrastructure and essential services, including the financial sector. It mandates national oversight and risk management practices.
EBA (European Banking Authority) guidelines on outsourcing apply to banks and financial institutions and offer direction on how to manage outsourcing arrangements, especially those involving ICT services.
EIOPA (European Insurance and Occupational Pensions Authority) guidelines on ICT and security risk management apply to insurance and pension institutions, focusing on governance, risk management, and incident handling related to ICT.
Let’s see how the different regulations and guidelines stack up:
| Regulation | Scope | Enforcement | Focus | Notes |
| DORA | Financial sector | Pan-EU regulators | ICT resilience | Central to all aspects of digital risk and compliance |
| GDPR | Personal data protection | Strict fines | Privacy | Partially overlaps in data management protocols |
| NIS2 | Network and information systems | National oversight | Broader cybersecurity | Complementary but DORA is prioritized in finance |
| EBA 3rd-party outsourcing | Banking sector | EBA guidelines | Vendor management | Integrated into DORA’s third-party risk framework |
| EIOPA ICT guidelines | Insurance sector | EIOPA guidelines | ICT governance | Largely replaced by DORA for covered entities |
While GDPR, NIS2, EBA, and EIOPA guidelines each address critical elements of privacy, cybersecurity, and risk, they operate within specific scopes or sectors. DORA brings these elements together into a unified regulatory framework specifically tailored to meet the needs of digital operations in the financial sector.
To summarize the differences:
-
Unlike GDPR, which centers on individual data subjects and privacy, DORA emphasizes the operational integrity of entire digital economy.
-
Unlike NIS2, which applies broadly across critical infrastructure, DORA focuses on financial institutions’ need to ensure continuity and manage third-party risk in ICT.
-
Unlike EBA and EIOPA guidelines, DORA is enforceable across all EU member states and provides specific mechanisms for oversight and accountability.
This integrated approach makes DORA a cornerstone regulation that connects other regulations and guidelines and raises the bar for digital resilience in finance in Europe.
07
DORA compliance technologies
Several vendors offer tools to streamline DORA compliance by providing:
-
AI-driven observability, to identify and respond to anomalies in real time
-
Compliance frameworks and data governance tools, that align with supervisory expectations
-
Fail-safe architectures and threat intelligence sharing tools, to rapidly disseminate information on cyber-attacks to the community at large.
Such platforms enable:
-
Continuous monitoring and risk assessment
-
Automated resilience testing
-
Secure access and identity management
-
Standardized incident documentation and audit readiness
A new dimension of technology support comes from generative AI adoption. Generative AI (GenAI) models are being piloted to automate compliance checks, generate incident reports, and simulate threat scenarios. Financial institutions are using GenAI to enhance red teaming exercises by crafting attack simulations, as well as drafting recovery and communication protocols in real time during cyber exercises.
While promising, it can also come up with generative AI hallucinations, draft realistic phishing emails, or mimic legitimate system responses. DORA compliance frameworks are expected to evolve to address these risks.
Enterprises should consider GenAI readiness assessments as part of their DORA roadmap, ensuring any deployment is governed and risk aware.
08
DORA compliance conclusions
DORA represents a paradigm shift in how the financial sector approaches digital risk. It emphasizes proactive risk management, cross-sector collaboration, and strong oversight of ICT dependencies. While the compliance journey may be complex, it can also be seen as an opportunity to future-proof operations against increasingly sophisticated cyber threats.
As of January 2025, organizations should not only aim for compliance but also strive to embed resilience as a core strategic priority. The benefits extend far beyond regulatory adherence, extending to enhanced trust, operational reliability, and a stronger position in the digital economy.
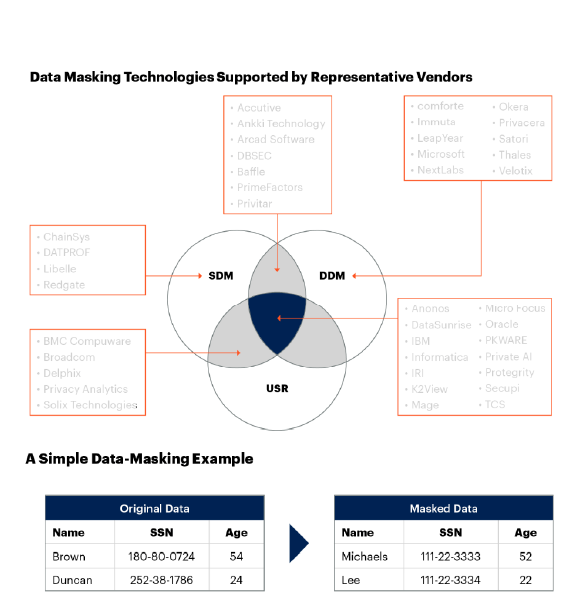
Technology partners can play a pivotal role in this transformation. For example, advanced data masking technology provides:
-
Automated PII masking
-
Structured and unstructured data masking
-
Referential integrity across all source systems
Enterprise-grade data masking reduces risk, improves compliance with DORA mandates, and simplifies operations across testing, development, and production environments. In doing so, it empowers financial institutions to make resilience an integral part of their operations.
09
Simplifying DORA compliance with K2view
As discussed above, one way to ensure DORA compliance – particularly in protecting sensitive data and reducing exposure – is by using Enterprise Data Masking (EDM) tools by K2view.
EDM lets you mask data in-flight, eliminating the need for staging environments where data might be vulnerable to exposure. It integrates data from multiple production systems, applies masking transformations, and ensures referential integrity across all data sources.
K2view supports both static masking for non-production environments and dynamic data masking based on user roles or environment context and meets DORA’s standards for ICT risk management and third-party access controls. For instance, those accessing test environments can receive masked data appropriate to their access level, significantly lowering the risk of both insider and outsider breaches.
EDM capabilities extend to unstructured data – such as PDFs, images, and documents – which are commonly overlooked by many data masking solutions. And its extensive library of prebuilt and customizable masking functions lets you tailor your masking to meet specific DORA compliance requirements quickly and painlessly.
In short, K2View not only supports DORA compliance but also helps you elevate your data protection posture overall.
Complimentary DOWNLOAD
Free Gartner Report: Market Guide for Data Masking
Learn all about data masking from industry analyst Gartner:
-
Market description, including dynamic and static data masking techniques
-
Critical capabilities, such as PII discovery, rule management, operations, and reporting
-
Data masking vendors, broken down by category
10
DORA compliance FAQs
What is DORA compliance?
DORA requirements focus on the cyber resilience of ICT systems. DORA benchmarks include:6
-
Independent parties must carry out annual resiliency and vulnerability testing. Regular threat-led penetration testing is also a requirement.
-
DORA requires protection measures that are risk-based and comprehensive. DORA security measures include taking a risk-based approach to network and infrastructure management; implementing appropriate and comprehensive policies for vulnerabilities such as patches and updates; using robust authentication mechanisms; and limiting the physical and virtual access to ICT system resources and data.
-
Procedures are required that “detect, manage and notify ICT-related incidents and shall put in place early warning indicators as alerts.”
-
Cybersecurity incident reporting is facilitated by having processes to monitor, describe, and report significant ICT-based incidents to DORA authorities.
-
DORA requirements on management and security accountability cover essential cybersecurity management and response for information sharing.
Is DORA applicable to the UK?
Although the Digital Operational Resilience Act (DORA) is an EU regulation, its influence will extend beyond EU borders—particularly into the UK financial sector.7
What are the 5 pillars of DORA?
DORA introduces a five-pillar framework of ICT risk management; incident reporting; digital operational resilience testing; third-party risk management; and information sharing.8
What is the DORA standard?
The Digital Operational Resilience Act, also known as DORA, is a pivotal EU regulation designed to enhance the operational resilience of digital systems that support financial institutions operating in European markets, with a comprehensive focus on risk management, incident response, and governance.9
What is the difference between DORA and NIST?
DORA is an EU regulation that took effect on 17 January 2025 to strengthen the IT security of financial entities and ICT third-party service providers, such as cloud or data analytics services. It aims to manage cyber risks for financial institutions holistically across the European Union.10
The NIST Cybersecurity Framework 2.0 was released by the U.S. National Institute of Standards and Technology (NIST) on February 26, 2024. It supports organizations in managing their cybersecurity risks by offering adaptable high-level outcomes to enhance assessment, prioritization, and communication of cybersecurity efforts.
The advantages of using both DORA and NIST 2 include:
-
Improved governance: DORA‘s new Govern function helps organizations know what is happening in each corner of their technology ecosystem. While NIST 2 focuses on integrating cybersecurity into systems and management. Governance provides structure for an organization to build cyber resilience and a proactive cybersecurity posture.
-
Comprehensive risk management: Using DORA and NIST 2 together supports organizations in creating a well-rounded risk management strategy. Holistic risk assessments ensure that vulnerabilities are uncovered before they can be exploited.
-
Better incident response: Detecting and responding to cyber threats promptly can improve the organization‘s recovery from cyberattacks. Implementing DORA and NIST 2 supports organizations in making incident response a priority and not an afterthought.
-
Third-party oversight: DORA imposes strict monitoring on third-party ICT providers, while NIST 2 helps evaluate third-party risks as part of an overall cybersecurity program. This dual layer of oversight reduces supply chain vulnerabilities.
-
Regulatory compliance: Both frameworks help ensure alignment with international regulations and standards, boosting trust with stakeholders and reducing potential legal risks.
Does DORA take precedence over NIS2?
This regulation applies to 20 financial entity types, spanning the entire ecosystem of banking, financial services and intermediary service providers. For these organizations, DORA takes precedence over NIS2.11
What is a DORA ICT provider?
DORA defines ICT services as “digital and data services provided through ICT systems to one or more internal or external users on an ongoing basis, including hardware as a service and hardware services which includes the provision of technical support via software or firmware updates by the hardware provider, excluding traditional analogue telephone services.”12















