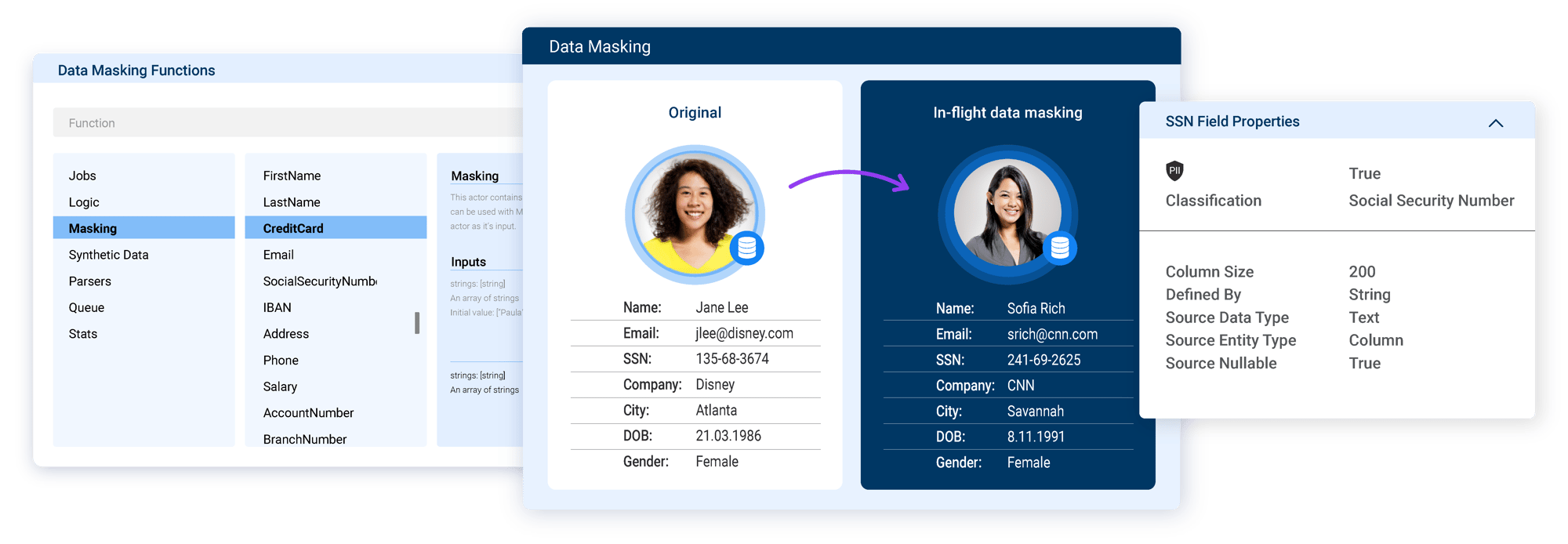

Protect sensitive data without compromise
In-flight and contextual
Data is masked in flight, in the context of its business entity, preventing sensitive data from ever being exposed
Referential integrity
Entity data masking enforces referential integrity of the masked data, regardless of data source diversity
Static and
dynamic
One tool for both static masking and dynamic masking, supporting any sensitive data use case
We made it easy for you to comply
- 01 PII Auto-Discovery
- 02 Dynamic and Static Data Masking
- 03 Unstructured Data Masking
- 04 All Data Sources
01PII Auto-Discovery
Locate your sensitive data
- Identify and classify sensitive data by scanning metadata and database content.
- Set up role-based (RBAC) and attribute-based (ABAC) access controls.
- Apply data masking rules and generate reports for full regulatory compliance.

02Dynamic and Static Data Masking
Data masking functions for any job
Mask data with your choice of:- 100s of built-in masking functions.
- Do-it-yourself masking functions, that can be reused.
- Dynamic data masking for operational use.
Static data masking for data analytics and software testing.

03Unstructured Data Masking
Anonymize PII from images and PDFs
- Protect sensitive data in unstructured files (images, PDFs, text files, and more).
- Generate synthetic, digital versions of receipts, checks, contracts, and more.
- Maintain referential integrity of masked data across structured and unstructured sources.
.webp?width=600&height=366&name=Data%20Masking%20new-03%20(1).webp)
04All Data Sources
Anonymize data across all data sources and platforms
- Integrate with any data source, technology, or vendor: on-premise, or in the cloud.
- Connect to relational databases, NoSQL sources, legacy systems, message queues, flat files, XML documents, and more.
- Ensure referential integrity through patented entity-based data masking.
.png?width=992&height=616&name=Data-masking-all-data-sources%20(1).png)
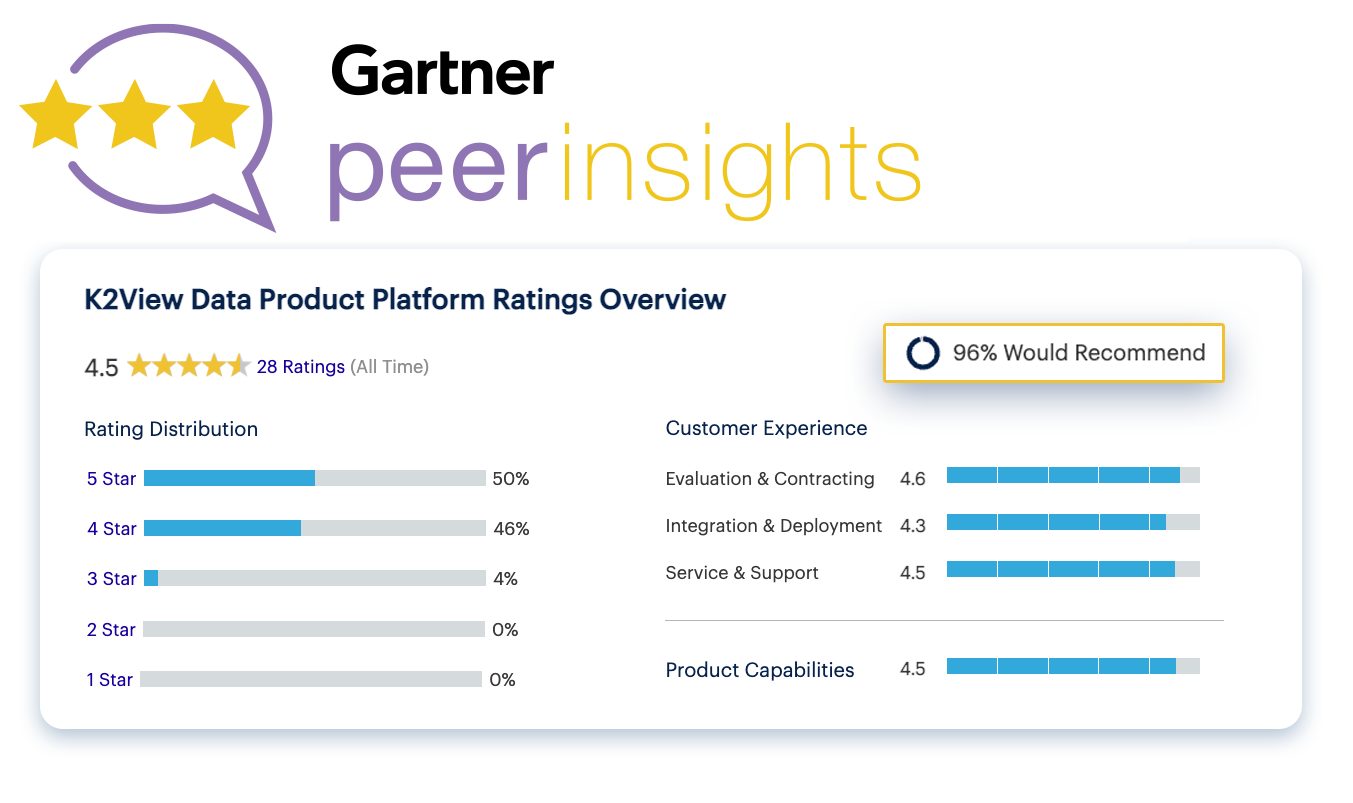
K2view gets top scores in Gartner Peer Insights
“High-end security for your sensitive information..."
“Innovative, fast and also scalable...”
“Excellent dynamic and static data masking...”
Benefits of entity-based data masking tools
Better data protection
Achieved with in-flight and in-context data masking
Greater productivity
Enabled by no-code tooling and prebuilt masking functions
Full automation
Integrates data masking into CI/CD pipelines
Quick and easy rollout
Implemented in weeks, instead of months
Flexible deployment
Available on-prem, cloud, or hybrid environment
Future-proofed
Designed to integrate with any and all data sources
Scalable
Optimized for high-performance at any scale
Lower cost
Eliminates per-database data masking software and fees
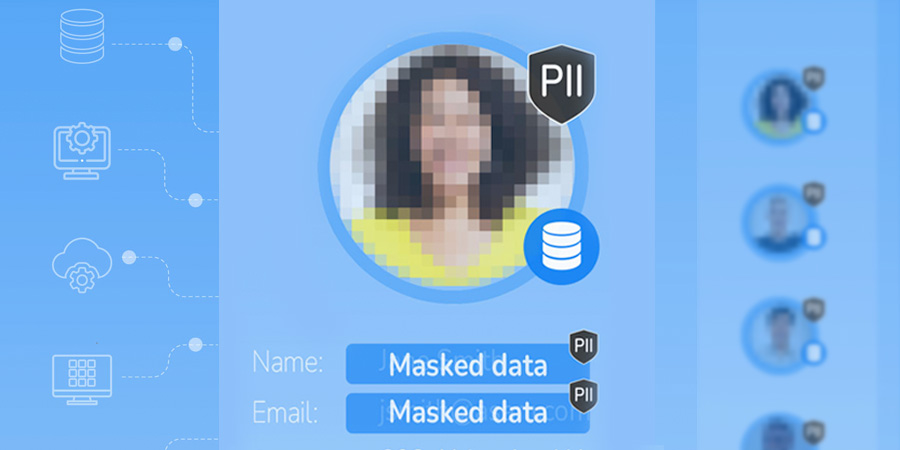
Entity-based data masking tools
Our patented approach makes all the difference
Auto-discover business entity schemas and auto-classify the PII and sensitive data for the business entities
K2view ingests multi-source data and automatically organizes it by business entities, in real time, to enforce referential integrity and facilitate contextual masking
Data is then masked in the context of the business entity and delivered to any target system or data store, with referential integrity preserved









.webp?width=1350&height=670&name=Anonymization%20vs%20masking%20(1).webp)
